1.2. AD RMS and Outlook
Some editions of
Microsoft Office can create and consume (open) IRM-protected content,
whereas other editions can only consume content (read-only). Table 1 outlines the IRM capabilities of the various Microsoft Office editions.
Table 1. Office Editions and IRM Content Protection and Consumption
| CREATE AND CONSUME IRM-PROTECTED CONTENT | CONSUME IRM-PROTECTED CONTENT (READ-ONLY) |
|---|
| Office 2003:
| Office 2003:
Standard Basic Small Business Student and Teacher Word Viewer 2003 Excel Viewer 2003 PowerPoint Viewer 2003
|
Office 2007:
Ultimate Enterprise Professional Plus
| Office 2007:
Professional Small Business Home and Student Standard Word Viewer 2007 Excel Viewer 2007 PowerPoint Viewer 2007
|
| Office Mobile (version 6.0 and higher):
| Office Mobile (version 6.0 and higher):
|
Office 2010:
Professional Plus Professional Professional Academic
| Office 2010:
Standard Home and Business Home and Student Office Starter
|
2. AD RMS and Exchange Server 2010
Assuming that an AD
RMS infrastructure has been established on the network, AD RMS can be
integrated with Exchange Server 2010 for automatic application of IRM
through transport rules and Outlook protection rules with Outlook 2010
defined by the Exchange administrator, and for manual application with
Exchange Server 2010 Outlook Web App and Outlook 2003 or higher.
Applying IRM to messages with Outlook uses the IRM functionality built
in to Outlook, and is independent of the AD RMS integration with
Exchange Server 2010. In Exchange Server 2010, if AD RMS is
implemented, voicemail messages marked as Private also have IRM
protection applied to them.
In Exchange Server
2007 and Exchange Server 2003 OWA, IRM functionality was limited to
reading messages only; you could not create new IRM-protected messages
or reply to existing ones. In addition, this functionality was limited
to Internet Explorer on Windows, and the AD RMS client had to be
installed on the computer if the operating system was not Windows
Vista, Windows 7, or Windows Server 2008 and higher. An IRM-protected
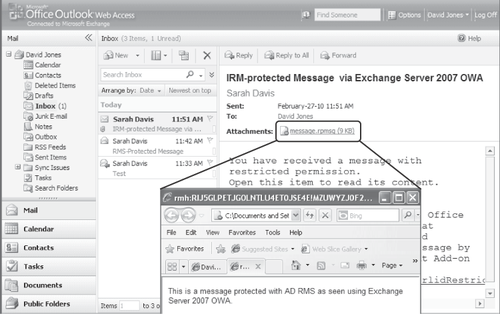
message as viewed in Exchange Server 2007 OWA is shown in Figure 5.
2.1. Protecting Messages with AD RMS
For an e-mail message to be protected using Outlook 2003, Outlook 2007, or Outlook 2010, the client computer requires the AD
RMS client to be installed; if the client operating system is Windows
Vista, Windows 7, Windows Server 2008, or Windows Server 2008 R2, the
RMS client is integrated with the operating system. The RMS client is a
separate download and installation if the client operating system is
Windows XP, Windows Server 2003, or Windows Server 2003 R2.
In addition, Exchange
Server 2010 provides the capability for the end user to apply IRM
protection to new messages manually and reply to IRM-protected messages
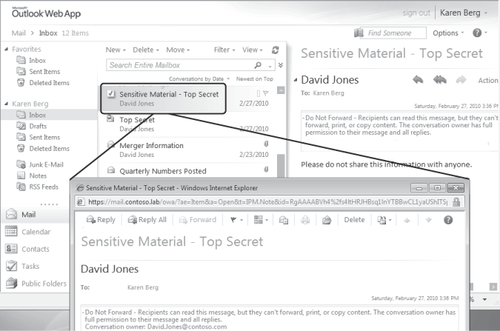
via Outlook Web App, using Internet Explorer 7 and higher, Firefox 3 and higher, or Safari 3 and higher, running on any client operating system. Figure 6
shows an IRM-protected message in Exchange Server 2010 Outlook Web App;
note that the message displays correctly in the Preview pane, and that
the Reply and Reply All functionality is available.
Exchange Server 2010
also provides you with the ability to apply IRM protection
automatically through transport rules on Exchange Server 2010 Hub
Transport servers and Outlook Protection Rules.
2.1.1. Outlook Protection Rules
Although users can apply IRM
protection to messages manually before they send them, they may
occasionally neglect to do so for messages that should be protected. Outlook
protection rules in Exchange Server 2010 can help in protecting your
organization from information leakage by applying IRM protection to
messages automatically when they are sent from Outlook 2010. When IRM
protection is applied to a message, any attachments in supported file
formats have IRM protection applied to them as well. Because Outlook
protection rules are applied within Outlook, the client must be running
Outlook 2010 because this is the only version of Outlook that can use
Outlook protection rules.
Outlook protection rules
are similar in functionality to transport rules that apply IRM
protection, but with the following differences:
With Outlook
protection rules, IRM is applied in Outlook 2010, before the message
leaves the user's computer. Transport rules on Hub Transport servers
apply IRM when the message enters the transport pipeline.
The
IRM protection applied with Outlook protection rules is also applied to
the copy of the message in the user's Sent Items folder.
Users
are aware if IRM protection is applied to a message with an Outlook
protection rule; when a message is protected by a transport rule, the
sender has no indication of this.
If
the Outlook protection rule allows it, users can choose to override the
protection applied by the rule. If the rule is overridden by the user,
an x-header named X-MS-Outlook-Client-Rule-Overridden is inserted in the message by Outlook 2010. By default, users can override the Outlook protection rule unless UserCanOverride is set to false.
Note:
Outlook
protection rules can be used to automatically protect content in
scenarios where you do not want to enable your Exchange servers for IRM
integration; for example, when the Exchange infrastructure is
hosted/managed by a third party. However, you need to be aware of the
following information if Exchange does not have RMS super-user permissions:
The Exchange server will not be able to perform content filtering or anti-virus filtering on protected content.
Exchange Server 2010 will be unable to apply certain transport rule predicates
or actions—such as when the Subject field or message body contains
predicates—or being able to append disclaimers to messages.
Protected
content will not be available through OWA, will not be journaled in
clear text, and will not be indexed or discoverable.
Outlook protection rules must be created using the New-OutlookProtectionRule cmdlet in the EMS; the following example creates a new Outlook protection rule that applies the Do Not Forward RMS template to messages sent to the Engineering distribution group:
New-OutlookProtectionRule -Name "Project X" -SentTo "[email protected]"
-ApplyRightsProtectionTemplate "Do Not Forward"
The following predicates can be used in Outlook protection rules:
FromDepartment
This predicate compares the sender's department attribute in Active
Directory to the department specified in the rule, and IRM protects the
message if there's a match. This will cause all messages sent by (for
example) the Research department with Outlook 2010 to be IRM protected.
SentTo The SentTo
predicate causes all messages sent to the specified recipient to be IRM
protected. For example, you can specify that all messages sent to the
Finance distribution group have IRM protection applied to them.
SentToScope
This predicate allows you to specify that messages sent inside or
outside the organization be IRM protected. This can be combined with
the FromDepartment
predicate; for example, you can create an Outlook protection rule that
directs that all messages sent by the Research department to internal
recipients have IRM protection applied.
When Outlook
protection rules are created, they are automatically distributed to
Outlook 2010 clients with Autodiscover and the Exchange Web Services on
Exchange Server 2010.
If you want to block any e-mail clients that do not use Outlook Protection Rules, you can implement blocking of all versions of Outlook except Outlook 2010 by using the Set-CASMailbox cmdlet with the MAPIBlockOutlookVersions parameter.
2.2. Consuming IRM-Protected Messages
IRM-protected messages
can be accessed with Outlook 2003, Outlook 2007, or Exchange Server
2010 Outlook Web App, assuming that the recipient has been granted
appropriate RMS rights to the message. To enable IRM for Outlook Web
App, the Federated Delivery Mailbox must be granted AD RMS Super Users privileges by adding it to the Super Users group defined for the AD RMS cluster; the Federated
Delivery Mailbox is a system mailbox created by Exchange Server 2010
Setup. The configuration of AD RMS for Exchange Server 2010
integration, including Super Users, is covered in detail in the Section 8.7.2.5 section of this chapter.
Exchange Server 2010 SP1 Outlook Web App also provides the ability to access attachments that are IRM protected using Web Ready Document Viewing.
Note:
Although
Outlook Web App provides the ability to read and reply to IRM protected
messages, unlike Outlook and other Office applications it can't prevent
users from performing screen captures by using Print Screen.
IRM for Outlook Web App and
Exchange ActiveSync (EAS) is enabled by default, and is available after
AD RMS is configured and the Federated Delivery Mailbox is granted AD
RMS Super Users privileges. To disable IRM for OWA and EAS, you can use
the Set-IRMConfiguration cmdlet with the ClientAccessServerEnabled parameter:
Set-IRMConfiguration - ClientAccessServerEnabled $false
Conversely, to enable IRM for OWA and EAS, set the ClientAccessServerEnabled parameter to true.
The Set-IRMConfiguration
cmdlet is used to disable or enable IRM for Outlook Web App for the
entire organization. If you want to enable or disable IRM for certain
Outlook Web App users, you can accomplish this with Outlook Web App
mailbox policies. IRM is enabled or disabled using the Set-OwaMailboxPolicy cmdlet with the IRMEnabled parameter.